| Hello, I'm a | software engineer. |
| hardware hacker. | |
| tinkerer. | |
| human being named TJ. |
Nice to meet you.
At a glance
- Name: TJ Horner
- Work: Site Reliability Engineer at Twosense
- Location: Redmond, WA
- Projects
- Blog
- Résumé
- Hobbies
- 📟 Hardware Design
- 💻 Embedded Development
- 🏠 Home Automation
- 🥘 Cooking
- 🚴 Cycling
- 🗺 Mapping
- Find Me Here
- Fediverse: @tj@tech.lgbt
- Twitter: @tjhorner
- GitHub: @tjhorner
- Telegram: @bcrypt
- Somewhere else? Probably @tjhorner
Work
I am a Software Engineer at Twosense where I work on the platform and backend teams, working with everything from low-level Windows driver APIs to modern web apps.
I previously worked at MakerBot where I made projects that integrated their extensive line of 3D printers with web-based products to better serve their education and professional customers.
Selected Projects
Here are some projects I am particularly proud of. You can view these and more on my Notion gallery.
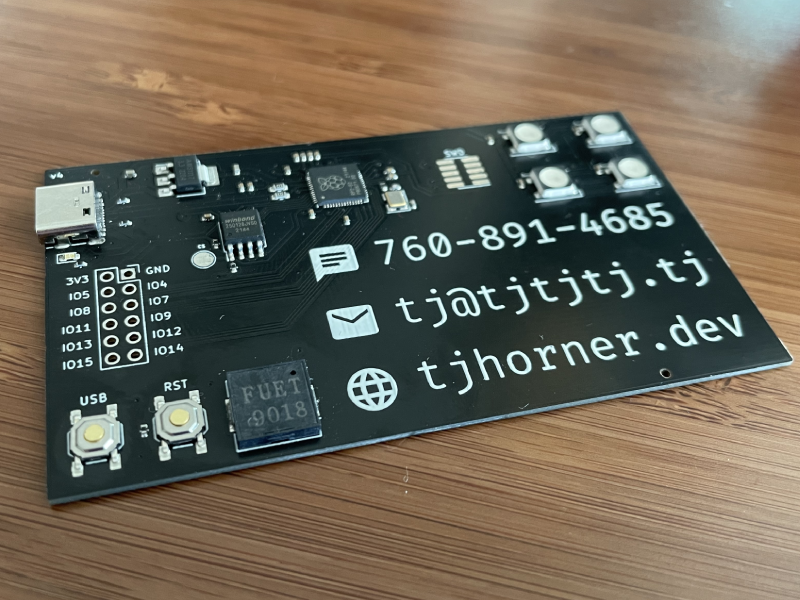
PCB Business Card
Functional business card powered by an RP2040

Upsy Desky
Connect your standing desk to home automation
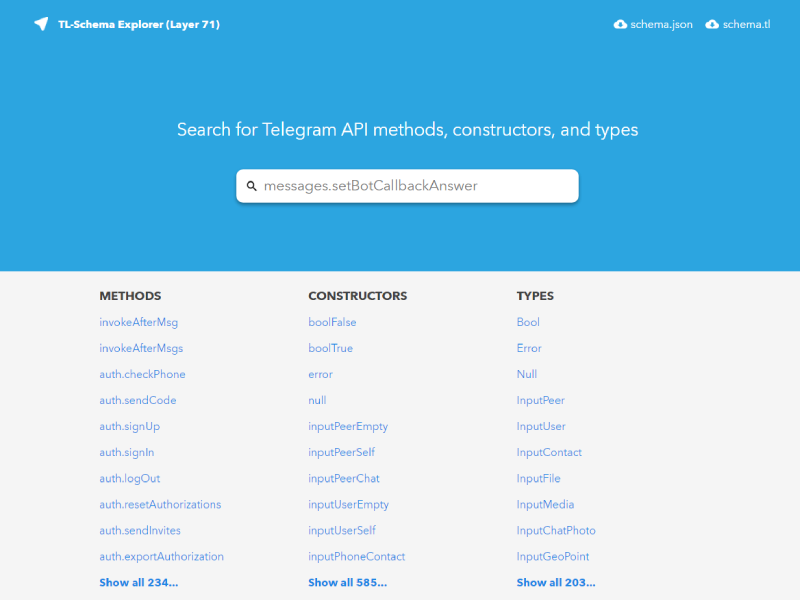
schema.tl
User-friendly Telegram API schema viewer
Experience
While I am principally a software engineer, I like to break out of my comfort zone and explore other interests like hardware, user experience, design, 3D art, and CAD in my free time. I learn best by doing, so I usually find a personal project to fuel my interest for a certain subject. You can see what I've done across all these disciplines on my Notion list of projects.
The skills I've picked up through these personal projects have worked their way back into my professional life — for example, if you visit the Twosense homepage (archive), you'll see a rotating DNA strand in the hero section. I used my Blender experience to create this asset for our website! I love collaborating with other teams on stuff like this, especially if they are close to what users see.
I also care deeply about making the things I create pleasant to use, and listening to users. I have previously volunteered at Telegram on their US support team, where I answered tens of thousands of questions from Telegram users, and interacted closely with the development team to make the product better. I apply the experience from this role in my daily work and try to have a deep empathy for users and consider their role as I build.
A good example of this applied experience is at MakerBot during our Thingiverse redesign. We ran into several issues and users took to Twitter to report them. I decided to use my personal Twitter account to talk to these users and hear them out. As a result our public presence was phenomenally improved, and we were able to fix more issues faster, and — of course — users were happier.